I wanted to present you a new plugin today. It was about switch idioms (jump tables). I spent a few hours trying to find a problematic x86 sample file but could not locate anything impressive. All jump tables were nicely recognized. This certainly does not mean that IDA handles them perfectly, but rather that my search methods must be improved.
Anyway, things were going nowhere and I decided to make a micro-break. It really helps to unblock the thought process (sometimes my entire working day consists of innumerable micro-breaks 🙂
I remembered that it is time to install security updates so I quickly downloaded them and looked into the details.
Sometimes I use the decompiler to find out the differences between programs: decompile two files and use a text comparison on the pseudocode. This simple approach works ok for short files: I found out the modified functions. There were two of them, the most interesting one named MRxDAVPrecompleteUserModeQueryDirectoryRequest() (what a name!)
The MS08-007 vulnerability is a classic buffer overflow: two unicode strings get concatenated into a buffer of a fixed size. The application checks the size before copying, so in theory there shouldn’t be any problems. I think that by looking at the following two screenshots you can tell why it didn’t work quite well. Before:
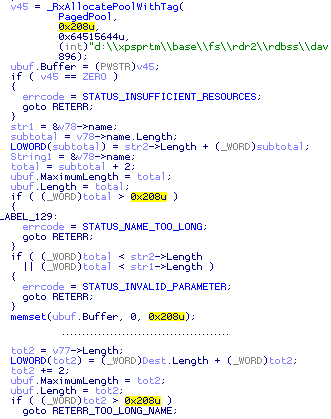
The old version was checking that the sum of the input string lengthes is acceptable. Unfortunately, the case of integer overflow is not handled.
After:
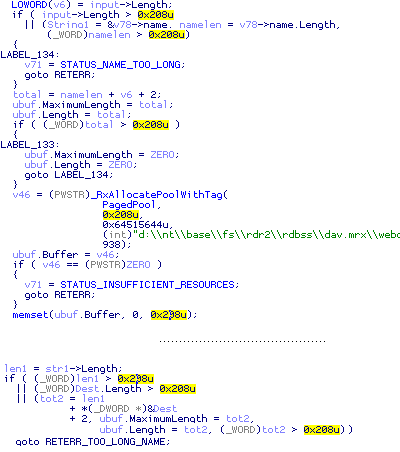
The new version checks three things: the length of each input string and their sum all must be acceptable.
A single highlight of 0x208 is enough to notice the difference. In the old version, only tot2 is checked against the limit.
Well, my micro-break turned into a blog post. Back to the plugin: I’ll find a nice sample file for jump tables and post a short video here. Stay tuned.
Stay up-to-date with the latest news!
Stay up to date with the newest blog posts.