

As everyone knows, Google and some other companies were under a targeted attack a few days ago. A vulnerability in the Internet Explorer was used to penetrate the computers.
An IDA user very kindly sent us the following link
http://www.avertlabs.com/research/blog/index.php/2010/01/18/an-insight-into-the-aurora-communication-protocol/
As it is visible from the screenshots, the code is somewhat nasty to analysis, because it consists of very short blocks like this:
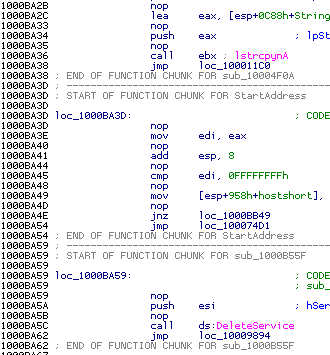
Even displayed in the graph mode, the output is still lengthy and messy:
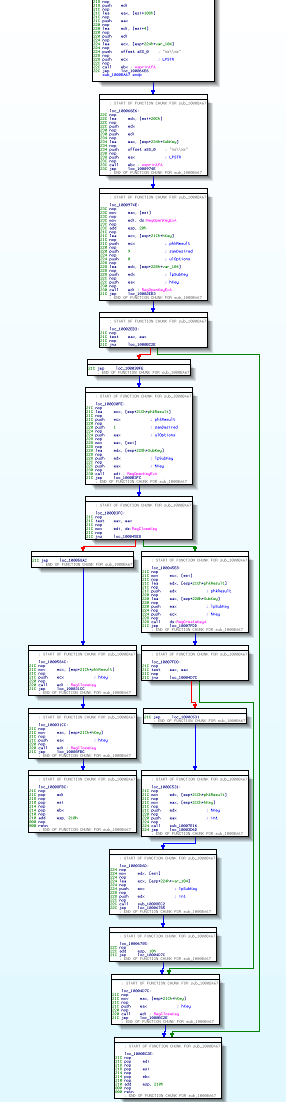
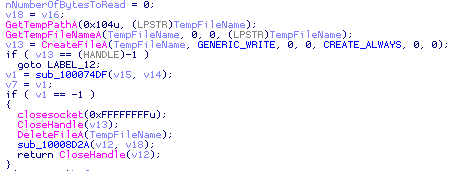
We were pleasantly surprised to see how the decompiler handles this code:
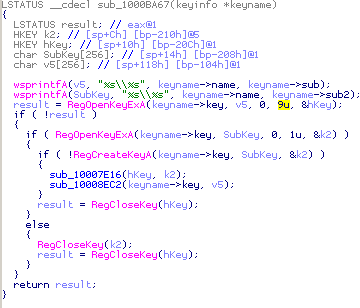
I renamed some variables and specified their types, but even without this, the output was very readable.
Just one more example. Virtually all functions are obfuscated with this quite simple technique:
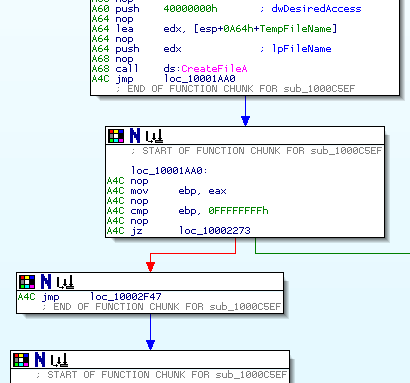
Yet the decompiler output is pleasing to the eye:
I’m very impressed by the results 🙂
We are currently completing support for intrinsic functions in the decompiler (it turned out that there are literally hundreds and hundreds of them). Also, SEE based scalar floating point computations will be mapped to high level constructs. It will probably take a few more weeks before the code stabilizes, it won’t be long. Thanks for being patient 🙂
Stay up to date with the newest blog posts