
This is a guest entry written by Markus Gaasedelen from RET2 SYSTEMS. His views and opinions are his own, and not those of Hex-Rays. Any technical or maintenance issues regarding the code herein should be directed to him, through the github.com repository.
Refreshing IDA’s Binary Patching Workflow
Patching assembly code to change the behavior of an existing program is not uncommon in malware analysis, software reverse engineering, and broader domains of security research. It’s an important practice that can be used to fix bugs, skip problematic (even dangerous) code, or augment software to make it easier to study.
As a long-time user of IDA Pro, I always felt teased by the fact that there wasn’t an easy and intuitive way to modify the assembly code it presents. This became the driving motivation behind my desire to build a plugin that could breathe new life into IDA’s patching experience.
An Interactive Patching Plugin for IDA Pro
Today, I am releasing a new interactive patching plugin for IDA Pro (7.6 and up) which is designed to accommodate fast-paced workflows that demand rapid iteration.
The plugin embeds several new contextual patching actions into IDA’s right click disassembly menus:
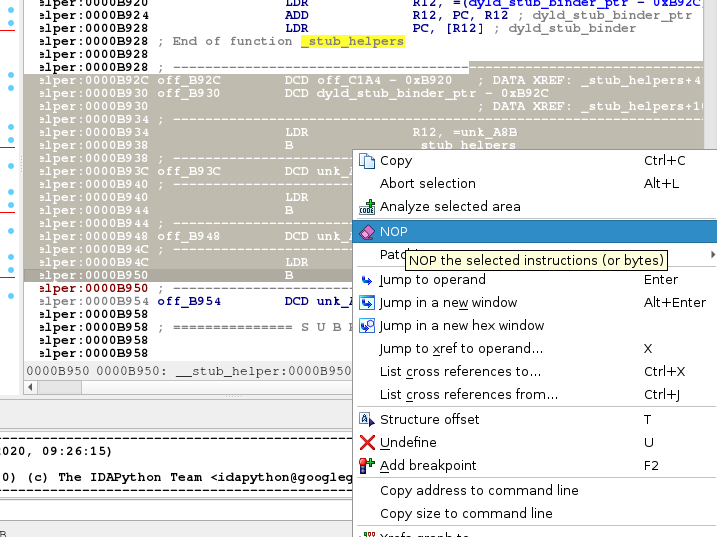
It also includes a dedicated dialog for editing or assembling new instructions:

As an initial release, the plugin only supports Intel x86/x64 and ARM/ARM64. In the next release, it will be extended to support some of the other popular architectures including PPC and MIPS.
Additional Information
A more complete description of the plugin and its features are available on GitHub. Going forward, the latest distributions of the plugin will be made available on the releases page. Please report any bugs or issues with the plugin directly to the GitHub repo.
Happy patching!
Thanks to Hex-Rays for supporting the development of this plugin!