

The Rust language is gaining popularity and nowadays even malware authors started using it, which means our users need to analyze them in IDA. The binaries produced by the Rust compiler have some peculiarities which make them difficult to analyze, such as:
While tackling all of them is a huge undertaking, which is further complicated by regular changes to the language, it is possible to handle some of the low-hanging fruits with modest effort. We’ve tried to first address the problem of non-terminated string literals and release this work-in-progress for our users to test and provide feedback on its performance with “in the wild” binaries.
While the current code does not cover all situations, it can handle the most common code patterns. For example, here’s a fragment of the same binary before using the plugin:
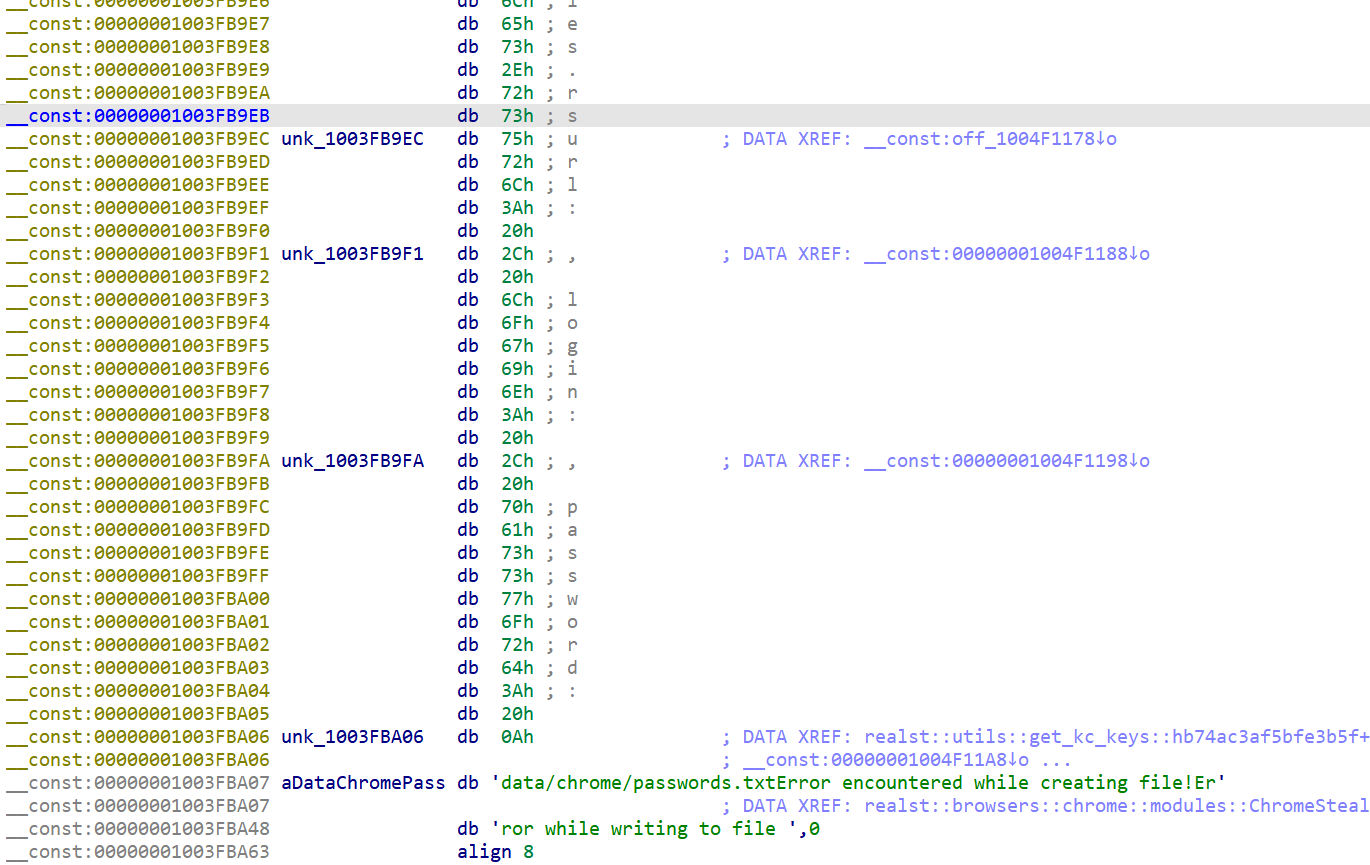
and after:

NB: the decompiled Rust code will probably still look ugly. Some changes will likely be needed in the decompiler or even IDA kernel to handle Rust’s code patterns properly.
Below are links to the current source code and builds of the plugin for IDA 8.3:
Stay up to date with the newest blog posts